This post is the second of the multiple infrastructure deployment with Terraform subject and in this part we will see how to use remotes backend in Azure.
One of great strengths of Terraform is maintaining the state of the environment it applies in a tfstate file. This file in Json format allows Terraform to apply only the differential for each execution. It is on this file that Terraform is based when executing plan/apply/destroy commands.
For more information about the tfstate read the official documentation.
Manage the tfstate for multiple environments and team
When we provision infrastructure with Terraform on several environments and that we work as a team, the usage of the tfstate can be more complex because:
- we need to use 1 tfstate file by environment
- the tfstate must be accessible by all the team members for manage the same infrastructure
- the accessibility of the tfstate must by secure, some sensitive information (like VM password) can be stored in
- the tfstate must be stored in backuped storage, in case of deletion, rebuilding it can take a long time
Taking this into account, we exclude the usage of the tfstate locally and the storage of the tfstate on source control manager.
For multiple environment provisioning we can use the
terraform planwith the option-state=<tfstate-filepath>, but the tfstate files are always locally and can be lost at any time.
The solution that will be used for the management of tfstate is to use the remote backend.
What is remote backend
In Terraform, the remote backend is remote and shared storage for store the tfstate file. When we use Terraform for provision Azure environment we can use Azure Storage Account for this remote storage.
Read the official documentation on remote backend here and remote state.
Use Azure Storage Account for remote backend
We’ve seen tfstate files attention points and introduced the remote backend, now we’ll detail technically how to use an Azure Storage Account for a Remote backend that will be used to store and centralize our tfstate files for each environment.
Create the Azure Storage Account
In your Azure subscription create an Azure Storage Account, and in the blob service create a container.
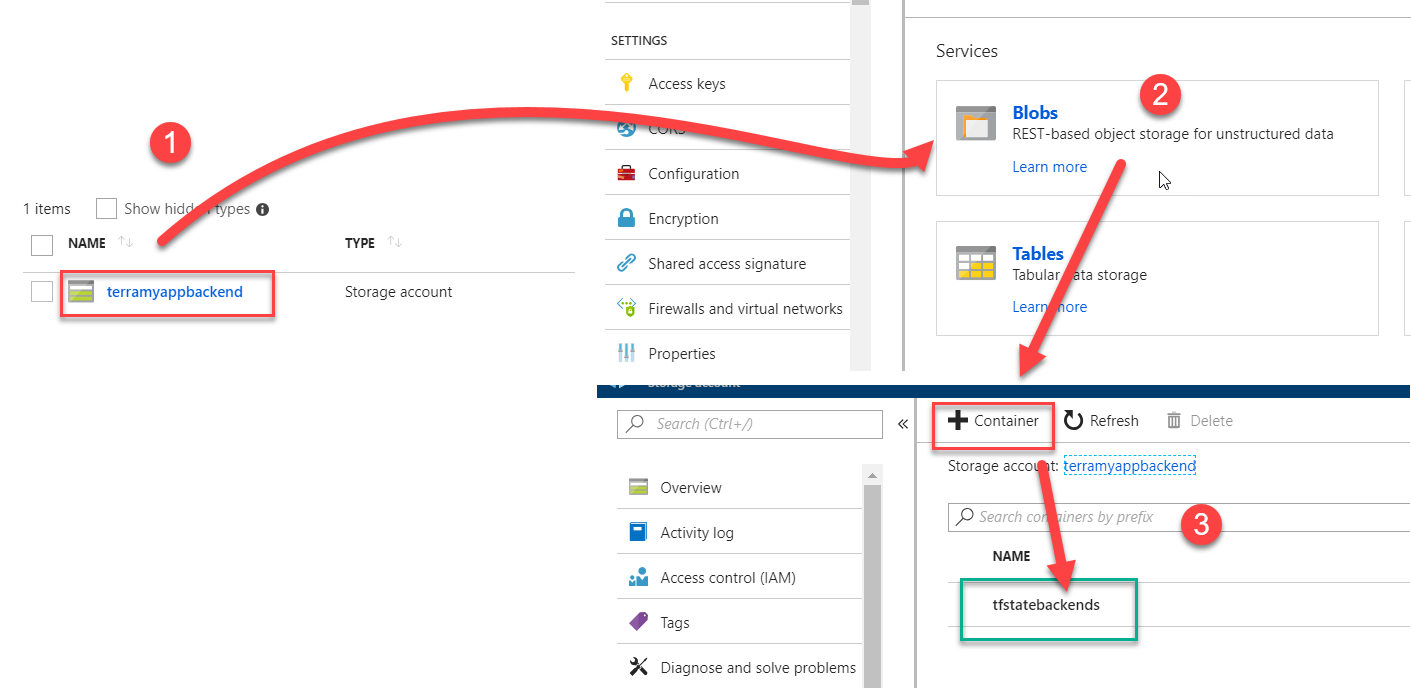
You can use at your convenience one container for store all environment tfstate or create one container by environment.
Configure the Terraform code
After the creation of the Azure Storage Account we need to configure our Terraform code for link it to our storage account.
Let us take again the schema in the directory seen in the previous article, and add a file backend.tfvars in each environment folder.
project
│ main.tf --> code that provisioning your resources
| variables.tf --> your variables declaration
└───dev
│ │ env.tfvars --> specific value of variable of the DEV env
| | backend.tfvars --> backend Azure storage configuration for DEV env
└───production
│ env.tfvars --> specific value of variable of the PRODUCTION env
| | backend.tfvars --> backend Azure storage configuration for PRODUCTION env
└───global_vars
│ global.tfvars --> common value of variables for all env
This file backend.tfvars contain the configuration of the Azure Storage Account:
resource_group_name = "hol-terraform-backend-rg"
storage_account_name = "terramyappbackend"
container_name = "tfstatebackends"
access_key = "p1EvkRL5ILVMQhIx7OP6q738EL7=="
key = "myapp-dev.tfstate"
resource_group_name is the name of the Resource groupe that contain the Azure Storage Account.
storage_account_name is the name of the Azure Storage Account.
container_name is the name of the blob container.
access_key is the Storage Account secret key.
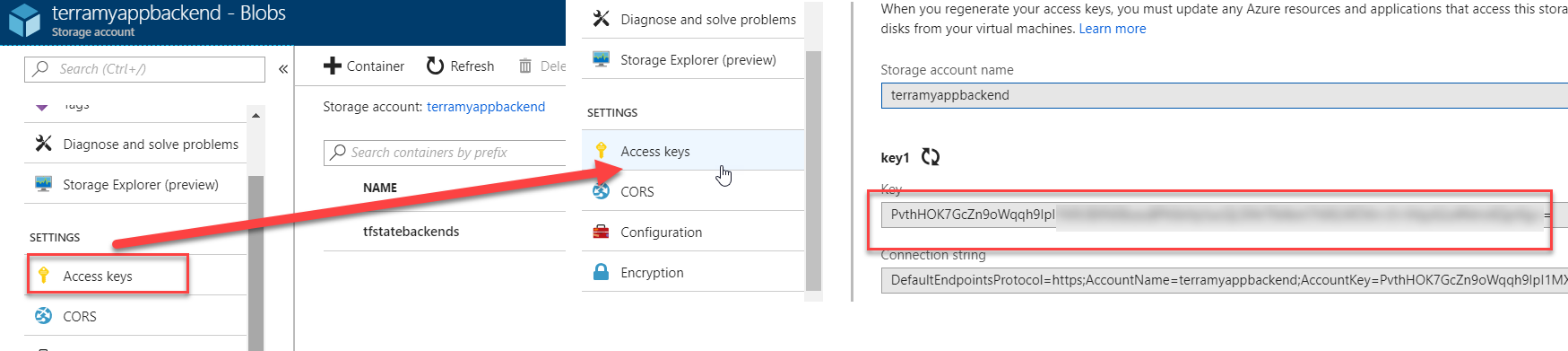
key is the name of the tfstate blob.
And in the content of the main.tf add the Terraform backend azurerm (leave empty):
terraform {
backend "azurerm" {
}
}
The Official doc on remote backends Azure here
Tip: If we use the same blob container for store all tfstate environment, we can create blob folder structure by environment with path on key parameter.
For example :
...
key = "dev/myapp.tfstate"
The dev folder is automatically created by terraform.
And in result we get one folder by environment:
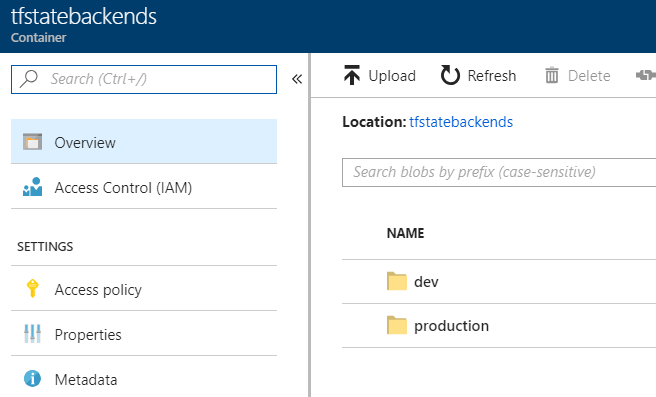
That all for the configuration !!
Init the Terraform execution with desired environment backend
After that the azurerm backend is configured in our code, we can initialize Terraform for use it.
The init is done by run the terraform init command and the -backend-config option.
At the root of the project folder execute the command:
For dev –> terraform init -backend-config="dev/backend.tfvars".
For Production –> terraform init -backend-config="production/backend.tfvars".
This command initialize terraform and connect it to the configured Azure Storage Account and tfstate file.
The documentation of the Init command is here for more details.
Summary
In this post we see how to use Azure Storage Account as Terraform remote backend for provision infrastructure on multiple environments. With this solution, the tfstate will be:
- shared for all team members
- securely stored for protect sensitive data and backuped
On the next post I will expose my some experience with Terraform Modules and how use the Terraform public registry with azureRM modules.
Comments